Weak Session Id Report
Session ID Vulnerability
Table of Contents
- Outline
- Vulnerability Explanation
- Proof of Concept
- Source Code Analysis
- Mitigating Weak Session ID Vulnerability
Outline
The goal of this write-up is to understand and predict DVWA Session ID creation process and thereby provide a detailed analysis of the vulnerability, its impact, and recommended mitigation measures.
Vulnerability Explanation
| Information | Explanation |
|---|---|
| Name | Weak Session ID |
| Severity | 8.0 |
| String | AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:A |
| Path | http://127.0.0.1/vulnerabilities/weak_id/ |
Session IDs are used to track and identify user sessions on websites or web applications. They are generated by the server and assigned to users upon login or when a session is initiated.
A weak session ID refers to a session identifier that lacks sufficient randomness or unpredictability. This makes it easier for attackers to guess or manipulate session IDs to gain unauthorized access to user accounts or perform session hijacking attack.
Proof of Concept
The tester first utilized Burp suite to intercept the POST request from the Generate button.
Burp suite is a powerful web application security and penetration testing tool. Upon intercepting the request, the tester sent the request to repeater and continuously sent the request to see how the Session ID changed.
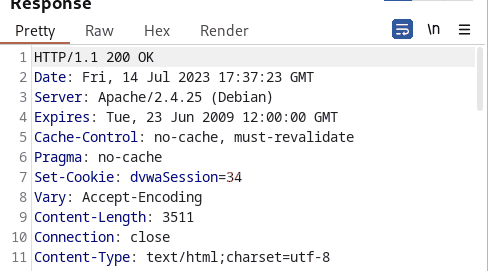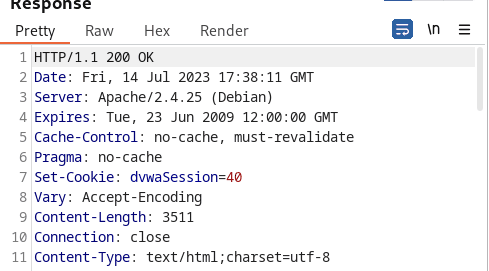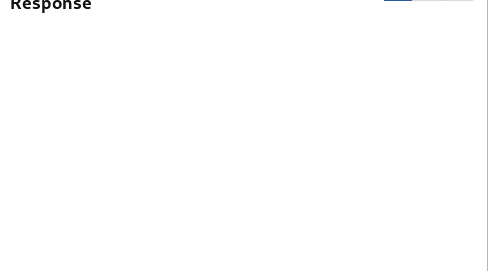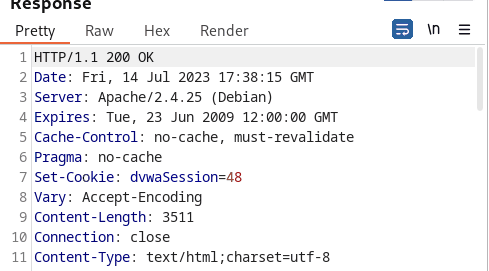
Examining the output, the tester easily predicted that the Session ID was increased by one. The tester also utilized Bursp suite’s sequencer tool to analyze the randomness and predictability of session tokens.
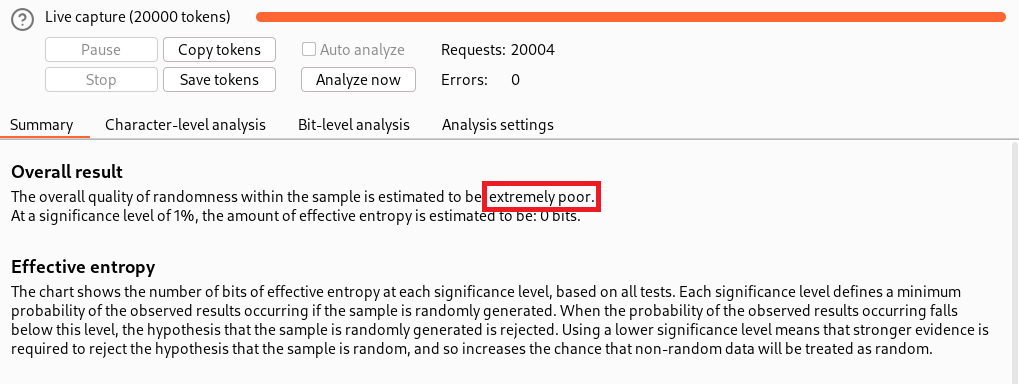
As expected, the overall quality of randomness is extremely poor with low entropy.
In the second scenario, the tester also intercepted the request to examin the change in Session ID.
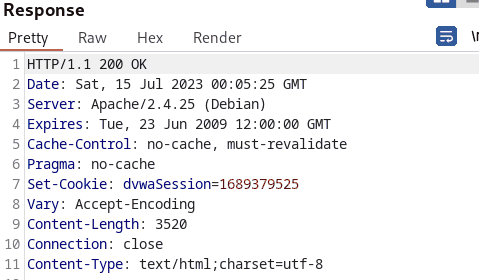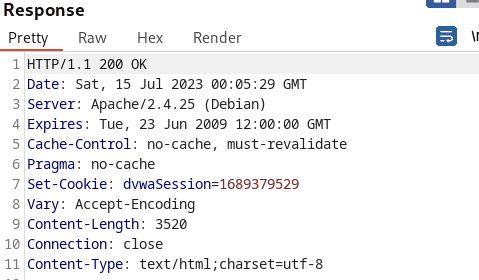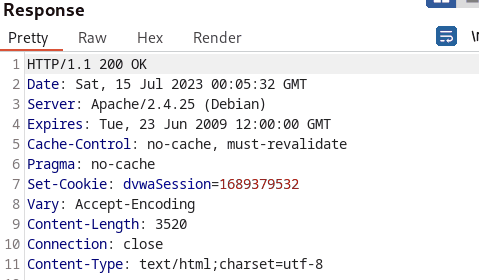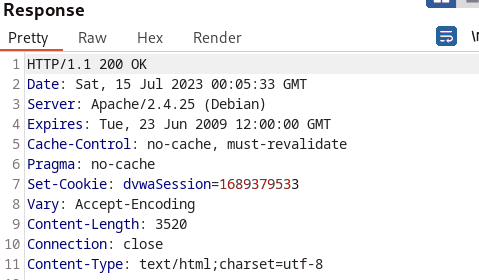
The tester noticed that the session_ids are sequentially incremented when the generate button was constantly pressed. However, the tester also realized that the Session ID values incremented according to the current time stamp.

The overall quality of randomness is extremely poor with a low entropy as well.
In the last scenario, the tester also intercepted the request to examine the change in Session ID. Although, at initial glance, the cookie values seem rather random and unpredictable, further analysis reveals that the values are md5 hashed.
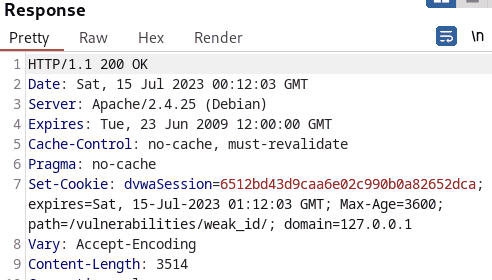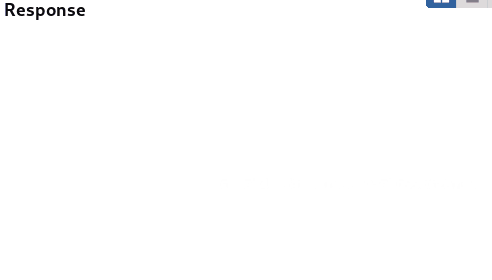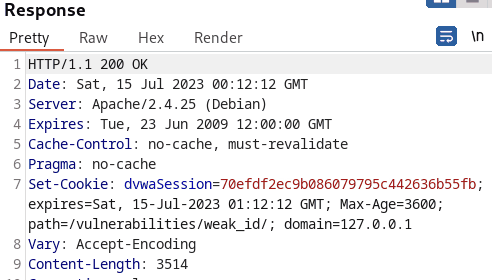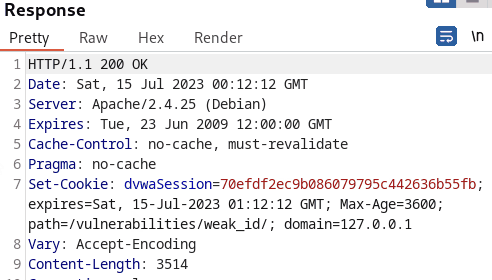
Cracking the hashes, the tester realized that incremental values were hashed with md5
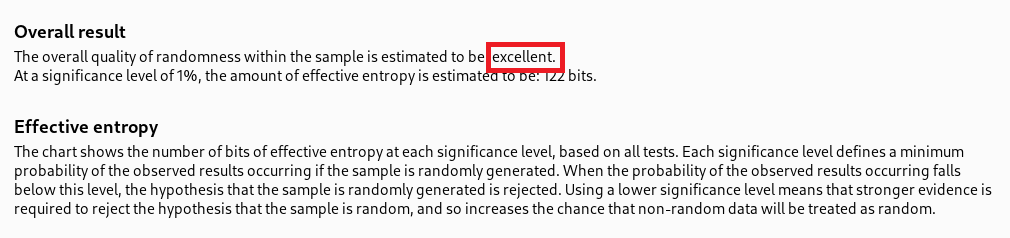
The overall quality of randomness is excellent with high entropy. This signifies that unless, the attacker successfully predicts the hashing algorithm, such hashing method provides a high randomness.
Source Code Analysis
Security-Low-Level
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id'])) {
$_SESSION['last_session_id'] = 0;
}
$_SESSION['last_session_id']++;
$cookie_value = $_SESSION['last_session_id'];
setcookie("dvwaSession", $cookie_value);
}
?>
In the Security Low Level Module the application exhibits a flaw in its session handling process. When the tester repeatedly clicked on the Generate button, the tester observed that the server responds with a Set-Cookie command, incrementing the value of the dvwaSession cookie with each request. This behavior allows an attacker to predict future and previous session cookies, enabling them to impersonate legitimate users and gain unauthorized access to sensitive information or perform malicious operations.
Security-Medium-Level
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = time();
setcookie("dvwaSession", $cookie_value);
}
?>
In the Security Medium Level Module the cookie values are set with the time() function. The output format aligns with the UNIX time. Similar to the Low Level Module the vulnerability arises from the lack of randomness and predictability in the session cookie values. The time() function generates session IDs based on the current time, which follows a predictable and incremental pattern. Attackers can take advantage of this predictability to guess or calculate the session IDs.
Security-High-Level
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id_high'])) {
$_SESSION['last_session_id_high'] = 0;
}
$_SESSION['last_session_id_high']++;
$cookie_value = md5($_SESSION['last_session_id_high']);
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulnerabilities/weak_id/", $_SERVER['HTTP_HOST'], false, false);
}
?>
In the Security High Level Module the cookie values are created and hashed using md5. The Session ID is set as the value of the dvwaSession cookie using the setcookie() function. The cookie is configured with an expiration time of 1 hour (time()+3600), limited to the /vulnerabilities/weak_id/ path. Although this enhances randomness and reduces predictability in session cookie values, the next Session ID was predictable as soon as the tester realized it was hashed with md5. md5 is a relatively weak hashing algorithm by today’s standards and was therefore easily crackable.
Mitigating Weak Session ID Vulnerability
Unpredictable, Random and Sufficient Length
Generate session IDs that are unpredictable. Session IDs should not follow a sequential or easily guessable pattern. Instead, it should be randomly generated using cryptographically secure random number generators. Use session IDs with sufficient length to safeguard from brute-forcing. Weak session IDs can be susceptible to brute-force attacks if they are too short. The recommended industry standard session ID must have a length of 128 bits or 16 bytes
// Generate a random session ID with sufficient entropy
$session_id = (random_bytes(16));
Add multiple layers of randomness by combining the current timestamp, a random number and hashing it with modern secure hashing algorithms, such as SHA-256 or SHA-3, for stronger security.
$cookie_value = hash("sha256", mt_rand() . time())
Session Expiration
Set appropriate expiration times for session IDs. Invalidate and expire sessions after a certain period of inactivity or after the user logs out. This reduces the risk of session ID reuse or session hijacking attacks.
// Set session expiration time and check for inactivity
function checkSessionExpiration() {
$sessionExpiration = 30 * 60; // 30 minutes (adjust as needed)
if (isset($_SESSION['last_activity']) && (time() - $_SESSION['last_activity']) > $sessionExpiration) {
// Expire session if inactive for the specified time
session_unset();
session_destroy();
// Redirect to login page or perform other actions
header("Location: login.php");
exit;
}
}
Secure Transmission
Ensure secure transmission of Session IDs by utilizing HTTPS. Session IDs should be transmitted securely to prevent interception and eavesdropping by attackers. Encrypting the communication between the client and server using Transport Layer Security (TLS) ensures the confidentiality and integrity of the session ID data. This security measure significantly mitigates the risk of Man-in-the-Middle (MITM) attacks during the transfer process.